LMNTRIX Adaptive Threat Response
A Validated and Integrated Threat Detection and Response Architecture
Overview:
The LMNTRIX Adaptive Threat Response is a validated and integrated threat detection and response architecture that hunts down and eliminates the advanced and unknown threats that routinely bypass perimeter controls.
Our cyberarsenal includes a combination of cutting-edge technology, leading intelligence, and advanced analytics which, when wielded by professionals with unparalleled expertise, allows us to detect and investigate the threats that others fail to even identify. Not only can we see the threats that others are blind to, we do so with great speed and accuracy.
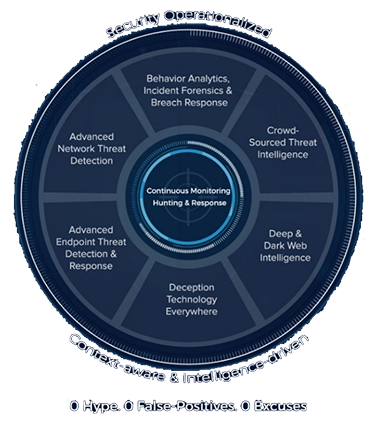
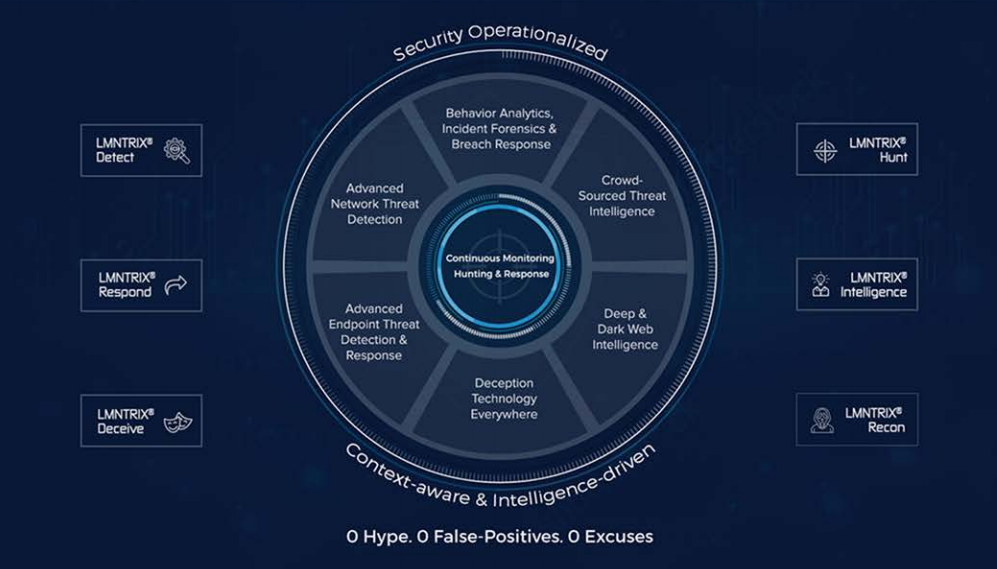
The technical aspect of our Adaptive Threat Response includes advanced network and endpoint threat detection, deceptions everywhere, analytics and real-time global threat intelligence technology. While these technologies are without peer, what sets us apart from the pack is our team of cyber professionals who continually monitor our client’s environments while simultaneously hunting threats internally as well as monitoring developments on the deep and dark web.
This combination of technology and expertise means our clients gain a fully managed service - delivered by the most experienced security analysts - that defends against the most determined and well-equipped adversaries. Whether the would-be attacker is deploying zero-day attacks, or is a government-sponsored advanced persistent threat, our cyber defense centers are vigilant 24/7, leaving assailants with nowhere to hide.
Ultimately, our goal at LMNTRIX is to give our clients a sober and realistic view of their cybersecurity - or lack thereof - in order to protect their business, their reputation and their data. By shining a light on the weak spots in their defenses and offering a comprehensive and seasoned alternative, one which doesn’t stop at the perimeter, we are able to stop more breaches, more accurately, with lower false positives and at a lower price than anyone else.
The LMNTRIX Adaptive Threat Response can be deployed in-house or consumed from the LMNTRIX Cloud. Our validated architecture is made up of the following elements:
The Nuts and Bolts
Adaptive Threat Response is composed of seven proprietary technologies. Each technology is powerful on its own. Put them all togther and that power is unprecedented. An offering so smart, so multi-faceted and so robust that attackers are quickly worn down and sent packing.
LMNTRIX Detect is designed to catch those threats, known and unknown, that bypass your perimeter controls. It uses a proprietary virtual sensor to deliver integrated, multi-layer detect-in-depth capability.
LMNTRIX Deceive is an attacker's worst nightmare. Deceive weaves an illusive layer over your entire network, coating every endpoint, server and network component with deceptions. If an attacker doesn't know what's real, an attacker can't act.
LMNTRIX Intelligence taps the power of the community to protect you. We all like PIE which in this case is our Predictive Intelligence Exchange. PIE aggregates over 100 threat intelligence sources and then we correlate these findings directly to your real-time network logs, mitigating threats long before others even know they exist.
LMNTRIX Respond service uses a light weight sensor deployed on all your endpoints to capture detailed state information and it is used by our Cyber Defense Centre to continuously monitor all endpoint activity, conduct adversary hunting, validate breaches and detect encrypted attacks. Using a light weight sensor our intrusion analysts delve deep into the inner workings of endpoints and expose anomalous behaviors.
LMNTRIX Hunt delivers extensive visibility, high performance threat hunting and unrivalled incident response by augmenting our Hunt Team’s capabilities with Behavior and Analytics technology.
LMNTRIX Recon shines a light on the deep and dark web by using our intelligence, knowledge and proprietary techniques to your advantage. Whether an attacker has stolen your data and is looking to sell it online or if someone is planning to breach your organization and is seeking advice on how to do so, we can use the attacker’s platforms against them so you can be certain of your defenses.
LMNTRIX ThinkGrid is a sophisticated, developer-friendly query language covering structured, unstructured, and time-series data. It is the perfect replacement for SIEM as it uses an open source search and analytics engine enabling scalability, reliance and extremely simple management.
Technology:
Adaptive Threat Response Platform
Often times, the difference between preventing a cyber attack or suffering a crippling loss is simply knowing where to look for the signs of a compromise.
Even the most advanced attackers leave traces of their presence so an effective defense must not only be vigilant, but also ever-adaptive in response to changes in attacker tactics. A critical element in this age of constantly evolving threats is a detailed view of an organization’s entire potential attack surface. Log collection solutions are simply outgunned against today’s advanced threat actors as they either lack the data, or the ability to analyze their data in a manner that allows rapid attack detection.
As a result, the LMNTRIX Adaptive Threat Response (ATR) platform is a must-have validated technology stack that improves our visibility and can be consumed as a service using the LMNTRX Cloud or on premise.
Our platform is based on a number of detective, responsive and predictive capabilities that integrate and share information to build a security protection system that is more adaptive and intelligent overall than any one system.
It is this constant exchange of intelligence - both between various aspects of our Adaptive Threat Response platform and with the wider cyber security community - that enables the LMNTRIX platform stay ahead of even the most persistent, well-resourced and skilled attack groups.
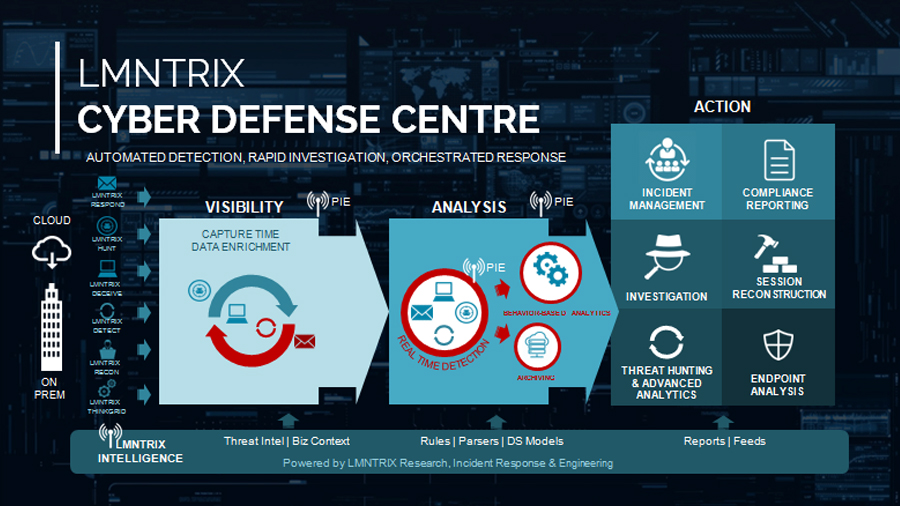
Security Visualized
The LMNTRIX Portal provides you with an overview of your entire network with the ability to cut through the static in order to respond to the highest priority threats via deep forensics and powerful collaboration tools.
Incident Response
The LMNTRIX Adaptive Threat Response platform aggregates threats from every one of the detective, responsive and predictive capabilities using standard protocols then it provides the required workflow to triage, investigate, escalate, and effectively remediate security incidents. The response procedure library is customized based on the threat category of each incident type. Additionally, the incidents are prioritized with business context so intrusion analysts investigate the incidents that pose the biggest risk to our clients.
Breach Response
After an incident has been positively categorized as a data breach, the LMNTRIX ATR platform enables our analysts to proactively manage the breach response process. Throughout this process, client incident and breach information is protected and shared only with the stakeholders that must know about it. Additionally, the LMNTRIX platform enables our team to assess the Confidentiality, Impact and Availability (CIA) of the breach which allows us to formulate client specific breach response plans. Each clients’ predetermined breach response procedures are catalogued in the response procedure library, allowing our analysts to respond rapidly when a breach is confirmed.
CDC Program Management
The LMNTRIX platform enables us to manage the overall effectiveness of our Cyber Defense Center (CDC) team from resources, scheduling, contacts, security controls efficacy and shift-handoff. With the use of the Program Management functionality we ensure that the overall CDC program is being managed as an effective, consistent and predictable process.
Multi-Threat Detection System
A proprietary virtual system powers our platform, delivering an integrated, multi-layered detect-in-depth capability which can be deployed on either dedicated or virtual servers. The MTD sensor connects with multiple clouds for updates, intelligence, policies, and cloud emulation and employs ten (10) threat detection modules.
Advanced Endpoint Threat Detection & Response
The LMNTRIX Advanced Endpoint Threat Detection and Response service uses a light weight sensor deployed on all your endpoints to capture detailed state information. Additionally, it is used by our Cyber Defense Center to continuously monitor all endpoint activity, conduct adversary hunting, validate breaches and detect encrypted attacks. Using a light weight sensor allows our intrusion analysts to delve deep into the inner workings of endpoints and expose anomalous behaviors.
Our techniques include live memory analysis, direct physical disk inspection, network traffic analysis, and endpoint state assessment. Our service doesn’t require signatures or rules. Instead, by leveraging unique endpoint behavioral monitoring and advanced machine learning, we dive deeper into endpoints which allows us to better analyze and identify zero-days and hidden threats that other endpoint security solutions miss entirely.
Armed with this information, our intrusion analysts instantly find similarly infected endpoints and quickly expand their visibility into the full scope of a compromise. Once an intrusion is confirmed, we disrupt malware-driven tactics, techniques and procedures (TTPs), and limit attacker lateral movement by quarantining and blocking the threat.
Hunting, Behavior Analytics and Forensics
Our platform delivers extensive visibility, high performance threat hunting and unrivalled incident response by augmenting our Hunt Team’s capabilities with Behavior and Analytics technology.
Our technology gives your network photographic memory. Full fidelity packet capture, which is optimized and stored for up to a year, means you will know with absolute certainty whether or not events have impacted your environment. Our platform is also able to detects threats in real time and automatically replay stored packets to discover previously unknown threats through the correlation of proprietary research intelligence, machine learning, flow-based traffic algorithms and multiple third party threat intelligence feeds.
Deceptions Everywhere
Our platform deploys deceptions everywhere to divert attackers and change the asymmetry of cyber warfare by focusing on the weakest link in a targeted attack - the human team behind it. Targeted attacks are orchestrated by human teams, and humans are always vulnerable.
By weaving a deceptive layer over every endpoint, server and network component, an attacker is faced with a false world in which every bit of data cannot be trusted. If attackers are unable to collect reliable data, their ability to make decisions is negated and the attack is stopped in its tracks.
Not only does this technique waste hackers' time, but it also allows the quick identification of attackers with high assurance. This is due to the fact that legitimate users have no reason to access the fake systems, vulnerabilities and information, allowing security teams to rapidly respond and prevent attackers from causing damage.
PIE - Predictive Intelligence Exchange
We are all facing attacks, all the time. As a result, we have a lot of data - why not share it?
That is the idea behind PIE: Attackers are known to share methods and tactics so, in order to advance the state of threat intelligence, organizations must collaborate and correlate more of their data, more quickly.
Today PIE aggregates over 200 threat intelligence sources with the aim of aggregating thousands more in the future. The proprietary technology behind PIE allows us to deliver earlier detection and identification of adversaries in your organization’s network. This is achieved by making it possible to correlate tens of millions of threat indicators against real-time network logs. This approach means threats can be detected at every point throughout the attack lifecycle, enabling mitigation before your organization experiences any material damage.
Deep & Dark Web Intelligence
It’s not enough to know what's happening on the inside of your network, you need to have someone who has your back on the outside too. After all, when hackers steal data, it almost always finds its way to an online black market - the deep and dark web.
We shine a light on this back alley of the cyber world by using our intelligence, knowledge and proprietary techniques to your advantage. Whether an attacker has stolen your data and is looking to sell it online or if someone is planning to breach your organization and is seeking advice on how to do so, we can use the attacker’s platforms against them. Our proprietary reconnaissance technology detects these and other cyberthreats in the deep and dark web by aggregating unique cyber intelligence from multiple sources.
ThinkGrid
LMNTRIX ThinkGrid is not a SIEM, but it is the perfect replacement for a SIEM as it uses an open source search and analytics engine enabling scalability, reliance and extremely simple management. It offers a sophisticated, developer-friendly query language covering structured, unstructured, and time-series data. Our use of machine learning algorithms means our platform gets smarter every minute while also eliminating the need for clients to write rules or create thresholds. By analysing your data in order to find discrepancies and unorthodox behavior, our platform is able to link these anomalies together, joining the dots and uncovering the truth behind advanced threat activity. Critically, in order to ensure accuracy, our algorithms are based on your data because the only way we can know what is “abnormal”, is to know what’s “normal” for your organization.
Adaptive Threat Response in Action:
Let's use a real-world example to show how Adaptive Threat Response stacks up. Deep Panda, or Shell Crew, continues to be a formidable threat group, actively attacking organizations and stealing data. Deep Panda is a prime example of an advanced persistent threat that is able to breach networks and then remain inside enterprises for years before detection.
The following diagram uses the Deep Panda threat profile to show how each element of the LMNTRIX Adaptive Threat Response works together to deliver unmatched threat detection and response.
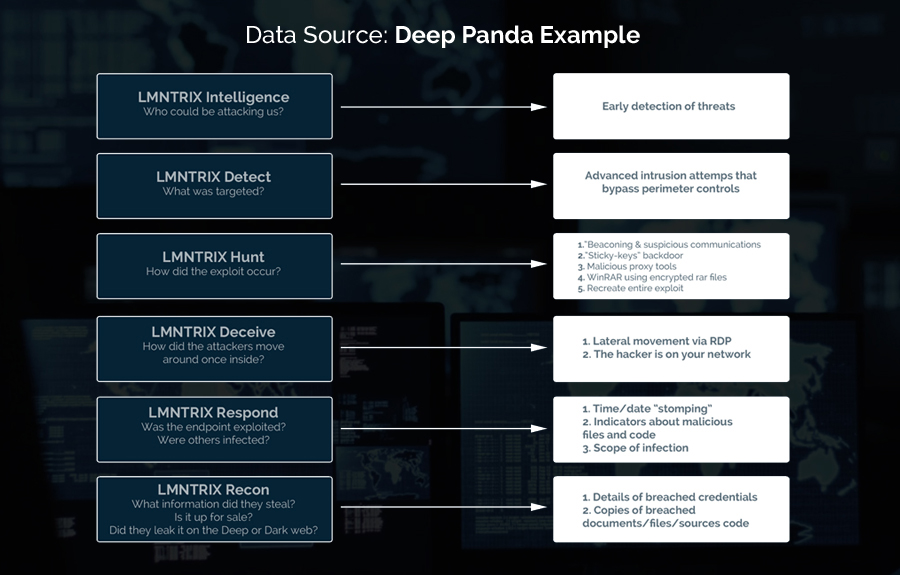
In the security community, Deep Panda/Shell Crew is also known as WebMasters, KungFu Kittens, SportsFans, and Pink Panther. Intelligence from RSA has found that Deep Panda’s general tactics, techniques, and procedures (TTPs) include;
- Prevalent use of Web shells to maintain low level persistence in spite of determined remediation efforts;
- Occasional use of Web application framework exploits to achieve initial entry as opposed to traditional spearfishing attempts;
- Lateral movement using compromised credentials with RDP, psexec, or network connections in conjunction with scheduling jobs with the "at" command;
- Abuse of Code Signing infrastructure to validly sign custom backdoor malware;
- Exploiting systems using different SETHC.exe methods accessible via Remote Desktop Protocol (RDP);
- Long history of IP/DNS telemetry allowing for historical research and link analysis;
- Placement of malicious proxy tools introduced into the environment on Windows server based proxies to bypass proxy logging;
- Extensive use of time/date stomping of malicious files to hinder forensic analysis; and
- Malware leveraging compromised credentials to bypass authentication NTLM proxies (proxy aware).
Deep Panda's Standard Exploit Pattern:
- Exploit known Web vulnerabilities
- Upload web shell and other tools
- Move laterally using Pass the Hash and other tools/techniques to gain Admin credentials
- Further Entrenchment using webshell, remote access, customized malware, etc to ensure persistence
- Stay undetected and Access Trade Secrets
What is the stick keys backdoor?
- StickyKeys is an accessibility feature to aid handicapped users on Windows computers.
- StickyKeys is activated by pressing the shift key five times in sequence.
- Works on networks where the systems have Microsoft Remote Desktop Protocol (RDP) enabled.
- Attackers exploit this vulnerability
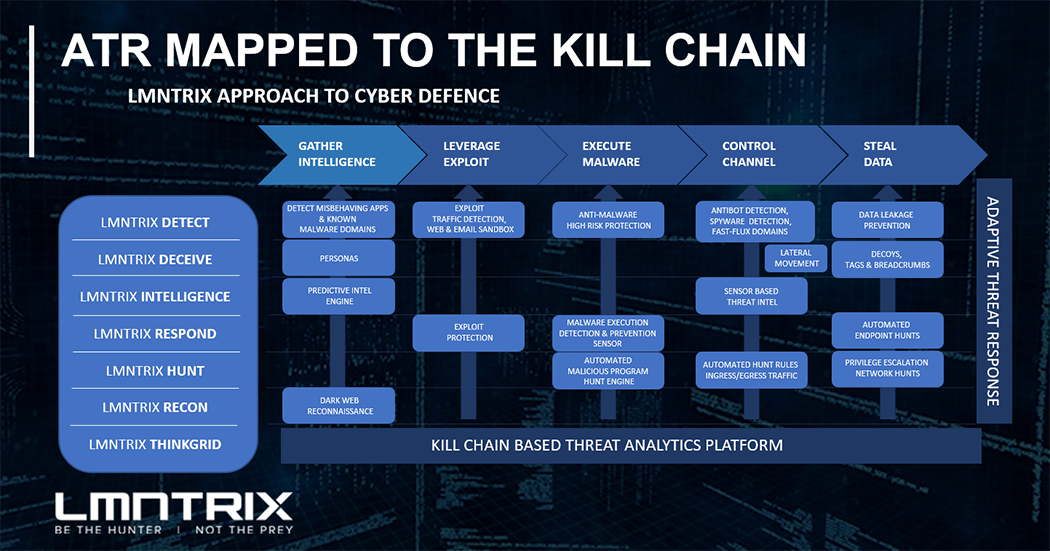
Adaptive Threat Response Mapped to the Kill Chain:
LMNTRIX Adaptive Threat Response (ATR) uses a validated and integrated threat detection and response architecture to hunt down and eliminate advanced and unknown threats that routinely bypass perimeter controls. LMNTRIX ATR was designed with a layered approach to cyber defense that maps to the kill chain intrusion framework and addresses all stages of adversary attack. Every one of the platform modules plays a crucial role to combat all advanced threats at any given stage of the kill chain.
Documentation:
Download the lmntrix adaptive threat response datasheet (.pdf)